Experts provide recommendations for establishing an effective crisis-communication framework:
- Create a cross-functional communication team. “We had an HR person. We had communication and legal people, and someone from the IT team,” Leach [chief technologist for HPE Security Services and a former chief information security officer (CISO)] says in describing the cybersecurity crisis-communication team at his former employer. Based on the type of breach, the core team sometimes brought in other in-house specialists. “So it might include a storage specialist, or a specialist from a line of business in another region of the world,” he explains.
- Establish a clear leadership structure. "When things happen, they happen fast,” De Souza says. “The communication tree needs to be well-defined, with an owner who is comfortable with taking charge.”
- Speak with one voice. That doesn’t necessarily mean using a single spokesperson. Instead, it means ensuring that everyone empowered to speak with stakeholders shares the same message. “In all of our communication, there were only two or three people who were allowed to speak for the company,” Leach recalls. He recommends providing those spokespeople with professional media training—again, well in advance of their need to use those skills.
- Have communication platforms ready to go. “People aren’t used to managing a crisis at the speed of Twitter,” Kawalec [CTO of HPE Security Services]. says. If the breach becomes public, put a dedicated website online as quickly as possible. Set up multiple two-way channels so that stakeholders—employees, customers, partners, the media, and others—can contact the company with information or questions.
- Practice, practice, practice. De Souza recommends running “tabletop exercises,” regular rehearsals involving communication strategies for responding to different types of cyberattacks. How regular? Souza [VP FireEye Inc.] says in the best examples he’s seen, organizations run drills every quarter and include the C-suite as well as the crisis-communication team. “You need to make sure the communication plan is operational and you can actually use it,” he notes.
Source: Crisis Communication After an Attack, MIT Technology Review, April 20, 2016
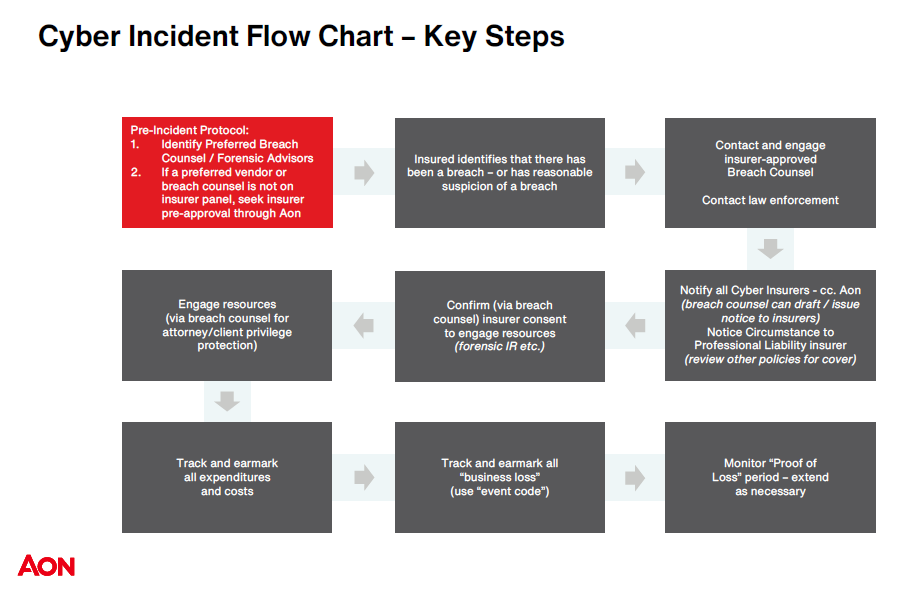
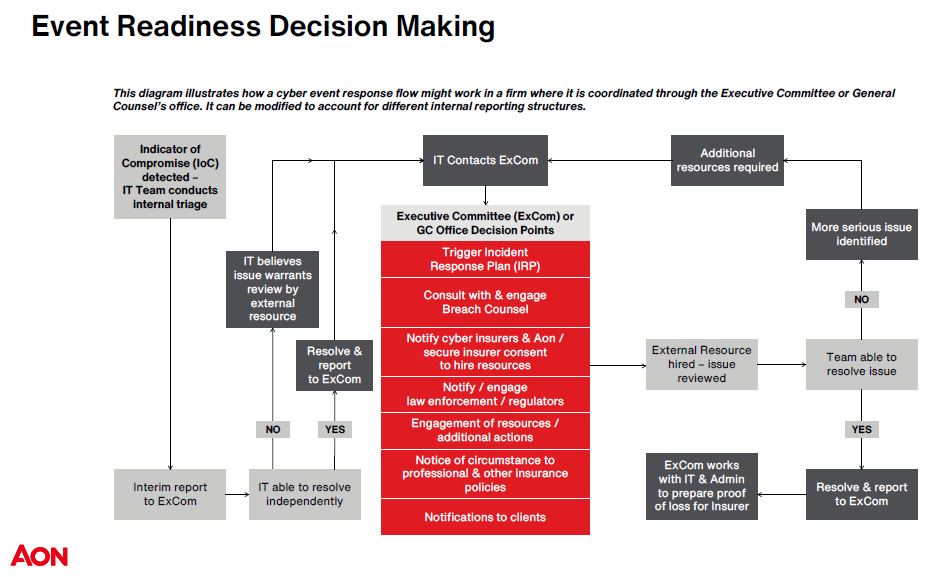
How to get started – frameworks
Cybersecurity is a huge topic and there is lots a firm could do in this area. Here are some frameworks you could use to create a plan to start improving your firm's cybersecurity (you're never done - it is an endless process).
For an overview of the issue and some tips you can us see the attached file from ILTACon 2016 "Security Awareness: A Blueprint from Start to Finish-ish"
Cyber Security Toolkit - Law Society (England & Wales)
Cyber Security Toolkit by Peter Wright
Overview
In today's digital world, law firms must ensure rigorous safeguarding of intellectual property, client data and other legal information as a crucial part of business strategy. Under Principle 10 of the SRA code, regulated firms have a responsibility to 'protect client money and assets' and cyber crime presents a significant risk to this.
As a result, cyber security is becoming a central issue for professional indemnity insurers and firms are being asked to demonstrate what protections they have against cyber criminals before they are [provided] PI cover.
This practical toolkit covers both the law and its practical application and will help ensure that your firm has effective policies and procedures in place to deal with cyber security. It will help your firm increase awareness of and be prepared for cyber incidents and the threats they pose, as well as how to prevent and deal with them. It will also [make available] assistance to help your staff comply with all their information security obligations.
As well as advice on how to safeguard digital information from both external and internal sources and examples of how to deal with issues such as information breaches in the workplace, it provides a number of precedents and templates on CD-ROM to ensure that your firm meets all of the legal and regulatory requirements to protect your personal and client data, such as:
- cyber crime risk audit
- mobile technology policy
- email security policy
- IT security checklist.
Quantity to order:
Top of Form
Bottom of Form
Contents
Part I: Understanding Cyber Security.
1. What is cyber risk?
2. Cyber risks within business structures;
3. Types of cyber attack;
4. The impact of a cyber security breach;
Part II: Mitigating Cyber Security.
5. Legal and regulatory standards;
6. Implementing and monitoring cyber security policies;
7. Staff training;
8. Network security and configuration;
9. User awareness and best practice;
Part III: Managing a Cyber Security Breach.
10. Reporting and response procedures.
Appendices. Useful contacts and links.
About the Author
Peter Wright is one of the UK's leading experts on digital issues in law firms. Peter is managing director of DigitalLaw UK Ltd and he is a solicitor and chair of the Technology and Reference Group at the Law Society.
Cybersecurity Best Practices Guide For IIROC Dealer Members
Investment Industry Regulatory Organizations of Canada developed to help their members better manage their cybersecurity risks. Much of it is applicable and useful for law firms.
"Key points in this report include:
- A sound governance framework with strong leadership is essential to effective enterprise wide cybersecurity. Board-level and senior management-level engagement is critical to the success of firms’ cybersecurity programs, along with a clear chain of accountability.
- A well-trained staff can serve as the first line of defense against cyber attacks. Effective training helps to reduce the likelihood of a successful attack by providing well-intentioned staff with the knowledge to avoid becoming inadvertent attack vectors (for example, by unintentionally downloading malware).
- The level of sophistication of technical controls employed by an individual firm is highly contingent on that firm’s individual situation. While a smaller firm may not be positioned to implement the included controls in their entirety, these strategies can serve a critical benchmarking function to support an understanding of vulnerabilities relative to industry standards.
- IIROC Dealer Members typically use third-party vendors for services, which requires vendor access to sensitive firm or client information, or access to firm systems. At the same time, the number of security incidents at companies attributed to partners and vendors has risen consistently, year on year. Firms should manage cybersecurity risk exposures that arise from these relationships by exercising strong due diligence and developing clear performance and verification policies.
"This Cybersecurity Best Practices Guide describes common practices and suggestions which may not be relevant or appropriate in every case. It is not intended as a minimum or maximum standard of what constitutes appropriate cybersecurity practices for IIROC Dealer Members. Effective management of cyber risk involves a contextual analysis in the circumstances of each Dealer Member."
Source: http://www.iiroc.ca/industry/Documents/CybersecurityBestPracticesGuide_en.pdf
Start with Security - Federal Trade Commission
"Lessons learned from FTC cases"
1. Start with security.
2. Control access to data sensibly.
3. Require secure passwords and authentication.
4. Store sensitive personal information securely and protect it during transmission.
5. Segment your network and monitor who’s trying to get in and out.
6. Secure remote access to your network.
7. Apply sound security practices when developing new products.
8. Make sure your service providers implement reasonable security measures.
9. Put procedures in place to keep your security current and address vulnerabilities that may arise.
10. Secure paper, physical media, and devices.
Overview
A security incident is an occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability of information, information systems or the processes of storing or transmitting information that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.
Purpose
This policy defines the requirements for reporting security incidents involving Firm Name information, and/or information technology resources to minimize the negative consequences of the incident and to improve the ability to promptly respond.
Scope
This policy applies to all Employees, Non-Partner Attorneys, Partner Attorneys, and Third-Party Vendors who have or are responsible for an account on any system that resides in Firm Name’s environment, or managed systems in the cloud.
Reporting
- Everyone at Firm Name has a duty to report all information security violations and problems to the Help Desk as quickly as possible so that prompt remedial action may be taken.
- Any of the following scenarios should be reported to the Help Desk. Once reported, the Security Team may need to respond appropriately:
- Confidential or Protected information is lost, disclosed to unauthorized parties, or suspected of being lost or disclosed to unauthorized parties.
- Loss of, or changes to production data. Any questionable usage of files, databases, or communications networks must likewise be immediately reported.
- Unauthorized system access is suspected or known to be occurring.
- Unusual and suspicious information-security-related events. These events include unusual requests for Firm information coming from an external party.
- Any irregular log-in screens, users must be suspicious of all pop-up windows, web sites, instant messages, and other requests for user IDs and passwords.
- Lost or stolen building access cards.
- Lost or stolen two-form authentication tokens.
- Damage to or loss of Firm computer hardware, software, or information that has been entrusted to your care.
- Loss of any device with Firm data resident on it. The Firm reserves the right to remotely wipe such lost device including all data and programs on the device whether or not the programs or data were furnished by the Firm.
- Any observations of suspected security weaknesses in systems or services.
- Suspected introduction of any malicious software (i.e., virus, malware, trojan).
- Firm Name will protect workers who report in good faith what they believe to be a violation of laws or regulations, or conditions that could jeopardize the Firm and its client’s information.
- Any attempt to interfere with, prevent, obstruct, or dissuade a member of the Firm in their efforts to report a suspected information security problem or violation is strictly prohibited.
- Anyone who reports a security problem, vulnerability, or an unethical condition within the Firm, at their sole discretion, may have their identity held in strict confidence.
- Workers who discover a weakness or vulnerability in the information security measures used by the Firm must not discuss these matters with anyone other than their direct supervisor, the Help Desk, and the Security Team.
Example: Cyber Incident Management Planning Guide For IIROC Dealer Members
The Investment Industry Regulatory Organization of Canada (“IIROC“) published this guide to assist member dealers plan for cyber incidents. Much of the guide is applicable to law firms.
To see the guide: http://www.iiroc.ca/industry/Documents/CyberIncidentManagementPlanningGuide_en.pdf
Incident response - top five mistakes in communicating
Taken from "The top 5 mistakes companies make in cyber crisis communications" by Siobhan Gorman 18 October 2017
Top mistakes:
1. Providing numbers or breach scope details
2. Publicly attributing the believed source of the attack
3. Ruling out data or systems affected (unless that data was never collected)
4. Ignoring media calls
5. Focusing on media response to the exclusion of customers or employees
Top things to do
1. Prioritize your stakeholders
2. Write all communications as if they will become public
3. Only provide data and facts you’re willing to stake your job on
4. Focus communications on the actions you’re taking
5. Take an action that demonstrates your commitment to improving cybersecurity
Source and to read more: https://www.brunswickgroup.com/the-top-5-mistakes-companies-make-in-cyber-crisis-communications-i6321/
.png?height=120&name=Lex_Mundi_Marque_White_RGB%20(003).png)